Utilizing user behavior analytics for classifying SAP security incidents efficiently
Enterprise Threat Monitor automatically analyzes SAP usage patterns and allows SOC teams to investigate and classify incidents efficiently. Let’s take a look at the following detected threat:
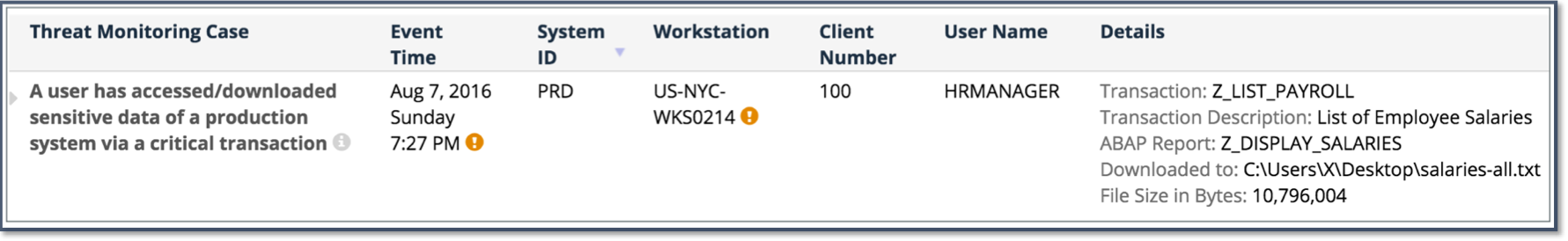
The finding shows that payroll information is accessed by HRMANAGER user and the event time and the workstation shows suspicious patterns.
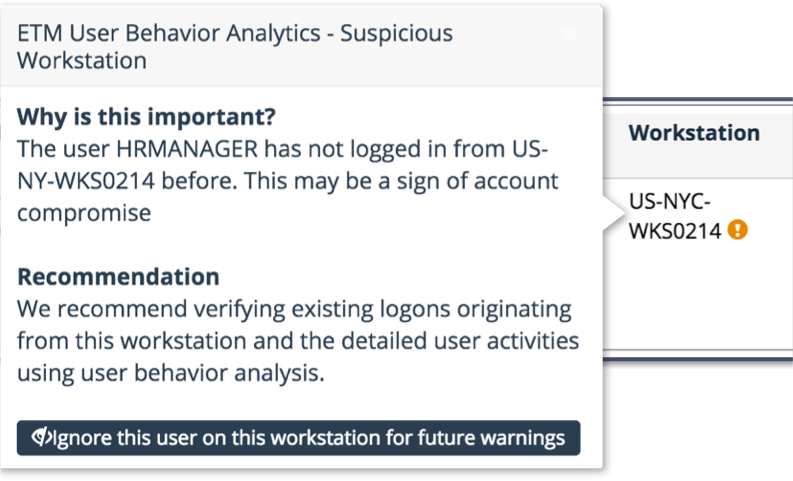
Incident or non-incident? HRMANAGER is supposed to access HR data
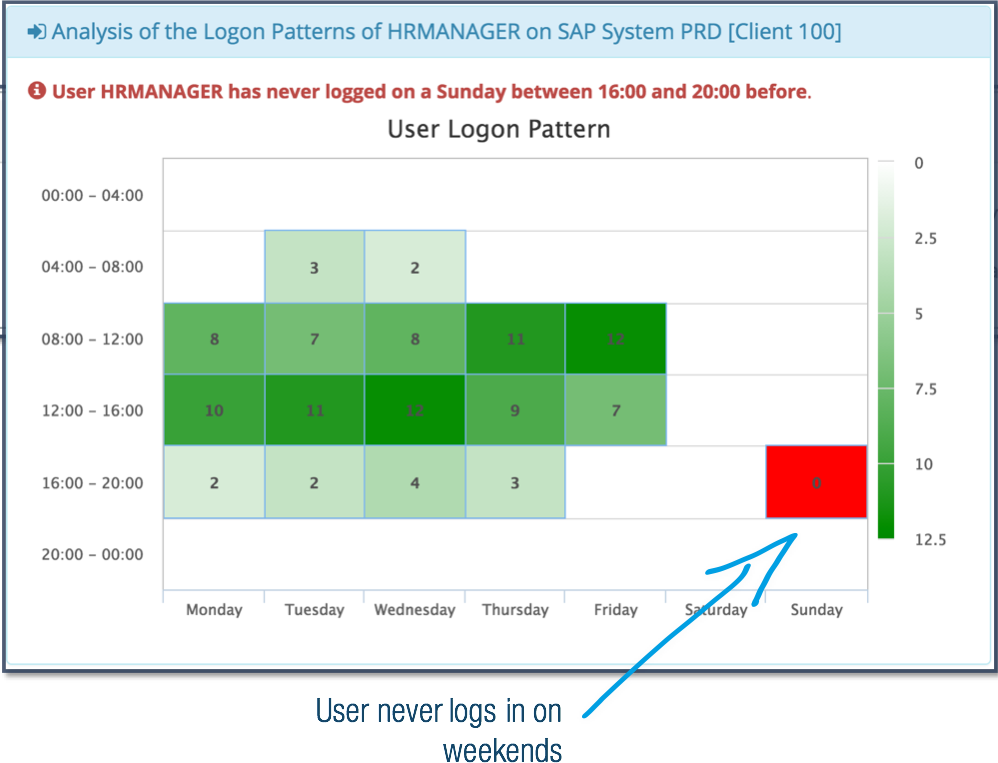
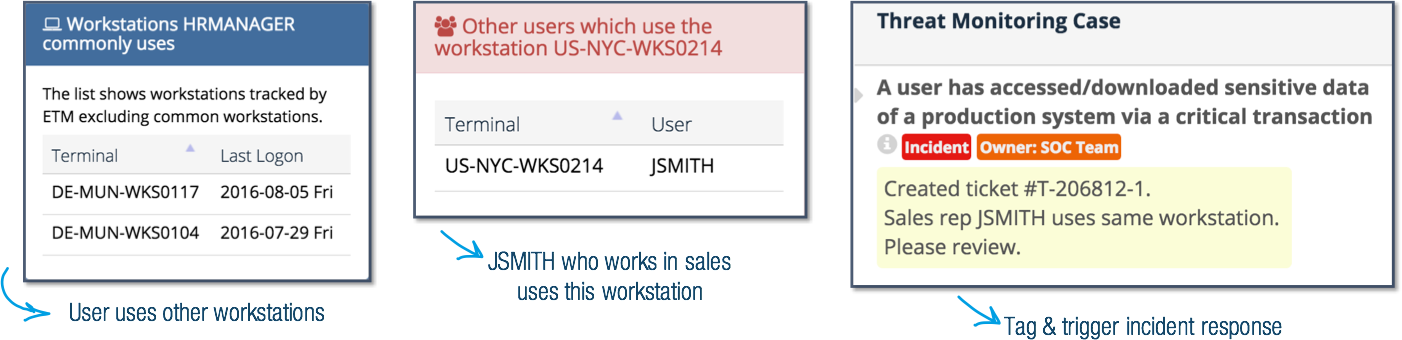
At first sight it appears that this user activity is a legitimate behavior. Further analysis reveals that this may be someone who obtained the account name and password of the HRMANAGER user.
By utilizing user behavior analysis, incidents can be distinguished from non-incidents efficiently